According to the State Special Communications Service, one of the most active and capable hostile hacker groups, the Russian Gamaredon (UAC-0010, Armageddon), has been involved in only 11 incidents of critical or high-level severity. However, as reported by experts, their activity has increased.
So, dev.ua asked the specialists from the State Special Communications Service which groups cause the most damage to Ukrainians and how many of them have Russian connections.
Hackers attacking Ukraine can be conditionally divided into three groups:
The first, and most dangerous, are military hackers. These are groups affiliated with Russian special services that work purposefully on our country's infrastructure, carry out orders, and have significant resources.
The second group consists of cybercriminals who cooperate with the Russian government but pursue their own selfish goals.
The third group includes so-called "hacktivists," individuals with varying levels of expertise who unite for attacks. They may be controlled by special services.
Who carries out cyberattacks on Ukraine? Among the most active hacker groups:
Armageddon / Gamaredon (tracked by CERT-UA under the identifier UAC-0010). In 2022, Gamaredon conducted more than a hundred cyberattacks on Ukraine.
Gamaredon is composed of hackers from the Yalta division of the FSB - former employees of the Security Service of Ukraine (SBU) in Crimea who betrayed their homeland and switched sides to work for the enemy. Gamaredon's primary goal is espionage. A distinctive feature of the group's phishing campaigns is the high level of their preparation, including knowledge of the Ukrainian context and an understanding of the specific operations of various organizations.
This group targets the state sector, state enterprises, the security and defense sector, and law enforcement agencies. For example, Gamaredon hackers attempt to gain access to all possible databases to extract information about vehicles, their movements, surveillance cameras, road conditions, arrests, and more.
Another active hacker group is Sandworm / UAC-0002 (UAC-0082 / UAC-0165), whose activities are associated with the Main Intelligence Directorate (GRU) of the Russian Federation. In January 2023, this group carried out a cyberattack on the Ukrainian National News Agency UKRINFORM. In April 2022, they targeted one of Ukraine's energy facilities using malicious programs Industroyer2 and CaddyWiper.
Last year, a group of cyber spies known as UAC-0056 (Pandora hVNC, RemoteUtilities, GrimPlant, GraphSteel) made multiple attempts to carry out cyberattacks. These are Russian state-sponsored cyber-activists. For example, there were several cases of sending dangerous emails with malware in 2022. They often use current themes and send emails from compromised email addresses of Ukrainian government bodies.
There is also UAC-0098 (TrickBot), a financially motivated hacking group that is currently acting in the interests of the Russian government. In April 2022, they conducted a cyberattack on Ukrainian state organizations by sending dangerous emails with the subject "Azovstal" and a malicious program called Cobalt Strike Beacon.
Group UAC-0035 (InvisiMole): These hackers are linked to Russia's Foreign Intelligence Service. The group conducts slow and "quiet" attacks aimed at espionage. Their main targets are high-ranking officials, diplomats, and other experts who have access to the most sensitive information. Because such "quiet" attacks are harder to detect, they can have more critical consequences.
Hackers from the group UAC-0028 (APT28) (also known as Pawn Storm, Fancy Bear, BlueDelta), which some researchers associate with Russian intelligence agencies, often direct their efforts against Ukraine:
-
In July 2023, CERT-UA detected an APT28 cyberattack aimed at stealing data from Ukrainians for accessing email services.
-
In June, through cooperation with Recorded Future, they uncovered a spying campaign targeting Ukrainian organizations.
-
In April, cybercriminals attempted to attack Ukrainian government entities with fake "operating system updates."
Group UAC-0100: This is a fraudulent group that operates with the aim of stealing funds from Ukrainian citizens. Their fraudulent activity is carried out by an unidentified group of individuals through the creation of fake websites and social media pages using themes like "financial assistance," "compensation," and "surveys" with the goal of stealing payment card data. In this case, it cannot be definitively stated that this group is associated with Russia.
In the first half of 2023, the Computer Emergency Response Team of Ukraine (CERT-UA) recorded continuous activity by at least 23 Russian cyberterrorist hacker groups. They all pursue various objectives, including military ones, and target both the public and private sectors.
In 2023, the most active groups were UAC-0010 (Gamaredon / FSB), UAC-0056 (Ember Bear / GRU), UAC-0028 (APT28 / GRU), UAC-0002 (UAC-0082 / UAC-0165 / Sandworm / GRU), UAC-0003 (UAC-0024 / Turla / GRU), UAC-0004 (UAC-0029 / APT29 / SVR), UAC-0109 (Zarya, group associated with Russia), UAC-0100, UAC-0106 (XakNet, group associated with Russia), UAC-0107 (CyberArmyofRussia, group associated with Russia). Registered cyberattacks were associated with these APT groups.

If we consider the distribution of incidents and threat actors (as presented above) and focus on the most critical and threatening ones (depicted in the figure below), it becomes evident that leading roles are played by the military intelligence teams of the GRU (Russian Main Intelligence Directorate) - identified as UAC-0056 (Ember Bear), UAC-0028 (APT28), and UAC-0002 (UAC-0082 / UAC-0165 / Sandworm. These three groups account for 50 serious incidents.
In contrast, the activities of the FSB team - UAC-0010 (Gamaredon) - have led to only 11 incidents of critical or high severity (as shown below) out of a total of 103 incidents associated with their Tactics, Techniques, and Procedures (TTPs), which we observed throughout the monitoring period across the entire spectrum of organizations reaching out to us or under our protection.
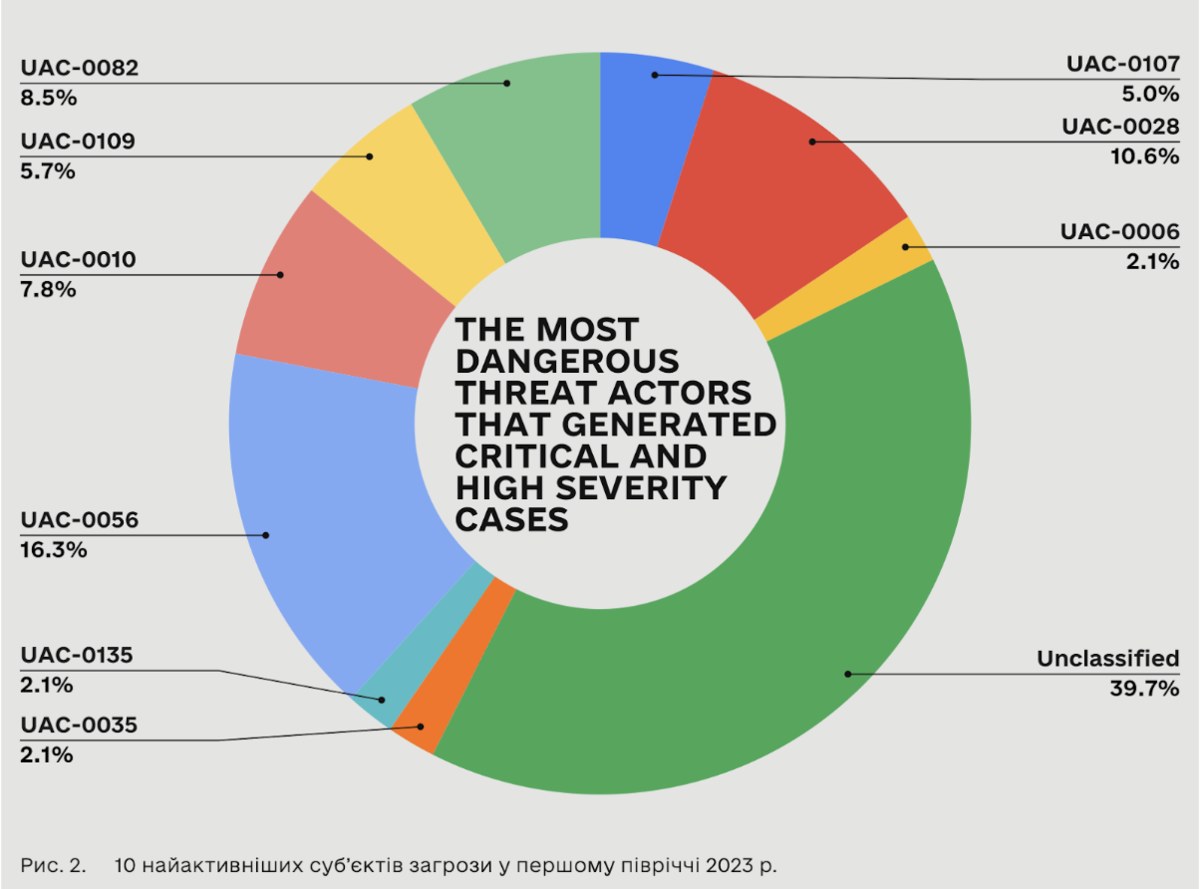
The analysis results indicate that the FSB cyber unit Gamaredon has significantly increased the overall number of operations. While CERT-UA registered 128 cases throughout the entire year 2022, there were already 103 cases in just the first half of 2023. However, not all of these incidents were as successful as before.
Most of the attacks were detected coming from groups such as Killnet, NoName057(16), XakNet, Anonymous Russia, and Cyber Army of Russia. All of these groups are associated with Russia.
These hacker groups actually cooperate with each other. They targeted the same or similar objectives and shared messages with each other on social media. However, their statements rarely describe the nature of probable cyberattacks.
During the first half of 2023, we noticed an increase in information operations with a cyber component. This category covers a wide range of actions, from coordinated atypical behavior on social media with the promotion of narratives related to Russia's war against Ukraine to alleged data leaks by "hacktivists" aimed at causing reputational damage.
Threat actors were publishing allegedly exfiltrated data (including through hacks and leaks) for various reasons:
- To prove their claimed interference.
- To damage the victim's reputation.
- To influence public opinion or as a sample of a larger dataset for sale.
More information on how the tactics, objectives, and capabilities of Russian government-linked hacker groups are changing can be found in the State Special Communications Service of Ukraine's analytical report, "Russia’s Cyber Tactics H1’2023." In this report, they analyzed and researched cyber threats from Russian hacker groups in 2022 and the first half of 2023, as well as changes in the behavior of cybercriminals.
The first year and a half of the war have shown that the potential of Russian hackers was somewhat overestimated. Russia, as it turned out, is not as strong as it was propagated in recent years. However, even though Russians have not achieved any strategic goals in their cyber aggression, it is clear that the enemy is cunning and dangerous and possesses significant resources. It is understood that they may use time to develop tools for further attacks on Ukraine. They are preparing for various scenarios in the cyber space, relying on the least optimistic ones.




















