The activity of the unnamed American company was linked to Ukraine. To access data related to these projects, Russian GRU hackers breached the company through its corporate Wi-Fi network using a new technique called "nearest neighbor attack." Cybersecurity firm Volexity detected a compromise on a server belonging to a Washington, D.C.-based client working on Ukraine-related projects, as reported by BleepingComputer.
APT28 hackers, part of Russia’s military unit 26165 of the GRU, have been conducting cyber operations since at least 2004.
Initially, they obtained access credentials to the corporate Wi-Fi network through password-spraying attacks on public services. However, multi-factor authentication (MFA) prevented the use of credentials through public networks. As connecting via corporate Wi-Fi didn’t require MFA, the distance from the victim posed a challenge.
The hackers creatively overcame this by searching for nearby organizations that could serve as a source for the target's wireless network. Their goal was to compromise another organization and find devices with both wired and wireless access. Such a device (e.g., a laptop, router) allowed the hackers to use its wireless adapter to connect to the corporate Wi-Fi network.
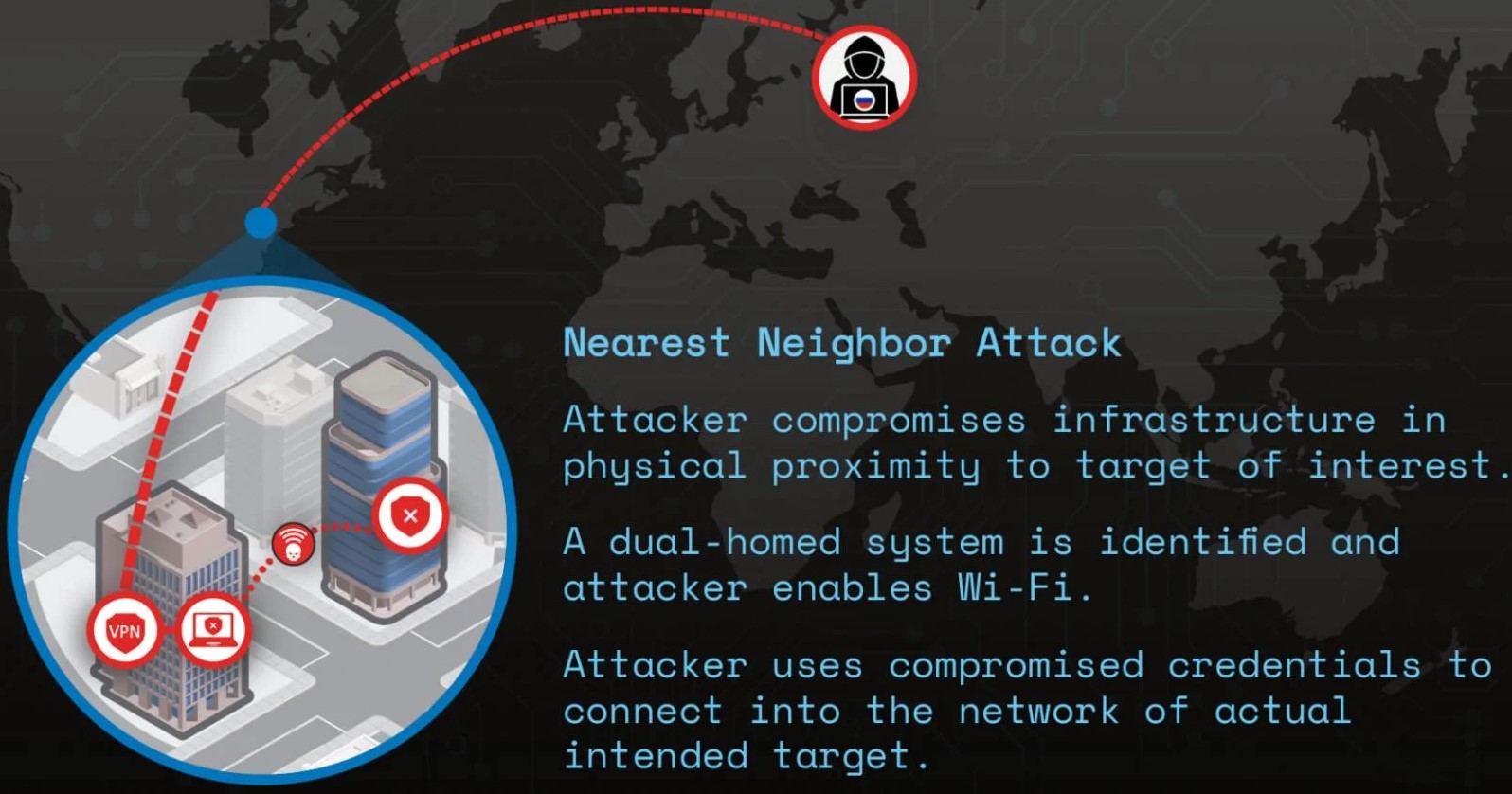
Volexity found that APT28 compromised several organizations as part of this attack, enabling connections with valid access credentials. Ultimately, they found a device within range that could connect to three wireless access points near the victim's conference room windows.
Using remote desktop protocol (RDP) with non-privileged accounts, the attackers moved within the target network, searching for valuable systems and exfiltrating data. They used the file servtask.bat to dump Windows registry hives (SAM, Security, and System), compressing them into a ZIP archive for further exfiltration.
The attackers relied on built-in Windows tools to minimize their traces while gathering data.
Volexity also confirmed that GruesomeLarch was actively targeting an organization focused on collecting data from individuals with experience in Ukraine-related projects.
APT28's "nearby neighbor attack" shows that a close-access operation, which typically requires proximity to the target (e.g. parking lot), can also be conducted from afar and eliminates the risk of being physically identified or caught.





















