The GRU is attacking networks across Europe using the malicious software Headlace, which steals information, and web pages collecting credentials. BlueDelta deployed the Headlace infrastructure in three separate stages from April to December 2023, using phishing, compromised internet services, and living off the land binary files to extract intelligence, as reported by Recorded Future.
The credential gathering pages are aimed at the Ministry of Defense of Ukraine, European transportation infrastructure, and the Azerbaijani analytical center, reflecting a broader Russian strategy of influencing regional and military dynamics.
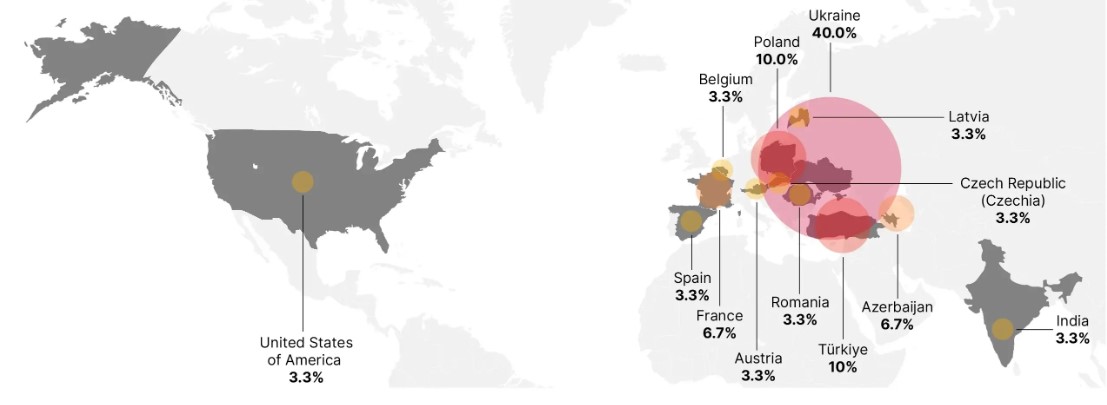
The GRU, as noted, continues to conduct sophisticated cyber espionage operations. From April to December 2023, BlueDelta deployed the malicious software Headlace in three separate stages, using geofencing methods to attack networks across Europe, with particular focus on Ukraine. The Headlace malware is distributed via phishing emails, sometimes mimicking legitimate messages for increased effectiveness. BlueDelta utilizes legitimate internet services (LIS) and living off the land binary files (LOLBins), masking their operations within regular network traffic. Such complexity makes detection difficult, increasing BlueDelta's success in compromising networks.
Successful infiltration of networks associated with the Ministry of Defense of Ukraine and European railway systems could allow BlueDelta to gather intelligence potentially shaping battle tactics and broader military strategies. Furthermore, BlueDelta's interest in the Azerbaijani Center for Economic and Social Development implies a program to understand and possibly influence regional politics.
To read the entire analysis, click here to download the report as a PDF.